Accessibility of crypto represents a problem, and if digital currencies are not to remain isolated in a niche economy focused on computer enthusiasts and political activists, this problem needs to be addressed.
Vulnerability of crypto that needs to be solved
Peter Schiff, known as a staunch opponent of Bitcoin, once tweeted that he had forgotten the password to his wallet, and therefore to several of his BTC. Later it turned out that he really lost everything.
This statement caused ridicule in the crypto sphere: many laughed at him, sometimes with open disdain, echoing his hostility to cryptocurrency.
Although he was responsible for this loss (he did not write down his recovery phrase or password), this case reveals an important thing about cryptocurrencies: they are not available to everyone. Indeed, many people may be affected by what Peter Schiff experienced: ordinary people do not try to find out how things work, especially in IT matters, and very often do not take the time to check that funds are safe. You only need to see the number of Bitcoins that have been lost since its inception and are still being lost today to get to the bottom of the problem.
A common practice to ensure availability and security is to transfer your cryptocurrencies to third parties, such as exchange platforms (Coinbase, Kraken, Binance, etc.), services specializing in storage (Coinbase Custody, Cryptob Objectif) or Satoshi application wallet or Tippin.me lightning. Thus, the number of such “custodial” solutions has increased so that investors can sleep peacefully and not allow users to complicate their lives due to the complex functioning of crypto-economic systems.
So this brings us to a broader question regarding the nature of adoption: can the democratization of cryptocurrencies be implemented in a decentralized way, or is it doomed mainly to these storage decisions?
Why Storage Solutions are problematic
Storage solutions have developed significantly and have become popular in recent years. In the early days of Bitcoin, its users (who were experienced professionals) installed the right programs to use the coin. But over time, this practice was limited to the microcosm of experts, and other holders mostly preferred to entrust their crypto assets to trusted third parties to avoid all the inconveniences associated with direct practice. Mt. Gox, the first major exchange platform to operate from 2010 to 2014, at one point owned more than 8% of the number of Bitcoins in circulation.
The hack on the Mt. Gox in 2014 and the huge losses of users` assets raised new concers. However, the following platforms were more scrupulous in terms of security, and gradually managed to earn a reputation: we can refer to the Kraken platform, which has never been hacked in nine years of existence. Custodial solutions have become more professional and adapted to regulatory requirements, and even if the risk of hacking is still present today, they often incur losses, as Binance did in May, 2019.
Thus, exchange platforms have turned into what we might call crypto-banks, which have all the advantages of traditional banks. A crypto bank will allow you to easily exchange your cryptocurrencies for fiat currencies, provide you with customer service, and distribute your staking income to you if you have a crypto asset like XTZ. And it is obvious that a very large number of users store their cryptocurrencies thanks to these crypto banks: how many people use their Coinbase account as a”wallet”? How many of them have never released their cryptocurrencies from exchange platforms? How many don’t even know it’s possible?
Crypto bank

This state of affairs would not be a problem if these custodial platforms did not have the disadvantages of banks. But unfortunately, this is the case, and therefore the use of crypto-banks decides what cryptocurrencies are useful for, namely, the complexity of censorship – resistant transactions.
Indeed, in many parts of the world, crypto banks are required to apply KYC (know your customer) identification. This means that if you use one of them, they will know who you are. This way, they can block your account or prevent you from making transactions if they want to, or if the state asks them to, usually under the pretext of preventing “money laundering”. Finally, if cryptocurrency is prohibited by the laws of your country, you will probably lose everything: both your keys and your coins.
This goes even further. The trend towards aggregation of digital currencies gives crypto banks considerable power over their future. In fact, exchange platforms already have a significant impact on the management of the Bitcoin protocol: when the chain is branched, they can refuse to list one branch in favor of another. Currently, this is offset by the fact that the vast majority of Bitcoins are stored outside of exchange platforms. But if the BTC becomes too popular, states can prohibit these well-identified platforms from doing so, and destroy the entire network effect of another version.
Thus, centralized storage solutions are problematic in the sense that their mass use can in principle weaken cryptocurrencies. This is what makes us wonder: is the mass adoption possible without passing them, that is, in a decentralized way.
This is a user experience (ux) issue. As we have already said, users prefer to leave their cryptocurrencies on exchange platforms for simplicity, because the current wallets are not convenient enough and are too reserved for technical specialists. They are not universal and widespread. Therefore, the user experience of decentralized solutions should become satisfactory enough for people to use them.
To do this, two basic conditions must be met:
- The user must be able to use the cryptocurrency from the device belonging to him;
- The user should not lose their cryptocurrency if they do not follow the recommendations.
Now let’s see if we can meet these two conditions and at what cost. We will mainly talk about bitcoin, but this also applies to all other cryptocurrencies.
First problem: access to the system

As we know: Bitcoin operates in a peer-to-peer network of nodes that exchange various information related to the block chain. These nodes, called “completed”, must consume memory space (the block chain, all utxos), bandwidth (accepting new transactions and blocks) , and processing power (checking transactions and blocks), so they require a good computer setup to work. It’s hard to see how Bitcoin could be democratized if everyone used these full nodes. Fortunately, while owning a full node provides a completely sovereign experience with Bitcoin, not everyone is designed to run a single node on their computer, and they are the alternative: a lightweight wallet.
As the name suggests, light wallets are wallets, meaning they give the user control over their money without requiring a trusted third party. However, unlike full nodes, they do not require the same computer resources, and can work, for example, on a smartphone. To do this, they use a method called simplified payment verification (SPV). This technique is not new and was described by Satoshi Nakamoto in section 8 of the official document:
“It is possible to verify payments without having to manage all the network node. The user only needs to keep a copy of the block headers of the longest chain of job confirmation, which he can get by polling nodes in the network until he is sure that he has the longest chain. As a result, you will get a Merkle branch linking the transaction to the block in which it is marked with a timestamp”.
Thus, this method allows portfolios to store only the block headers that make up the chain: the blocks are really composed in such a way that the block chain is reduced to a chain of headers. At 80 bytes per header today, this amounts to about 47 million data that is easily managed with modern devices. Wallets also do not process all transactions, but simply request transactions from nodes that they are interested in. They can then verify that their transaction was included in the block by querying data related to the Merkle tree of the block, reconstructing the branch that contains the transaction, and comparing the resulting root with the root recorded in the block.
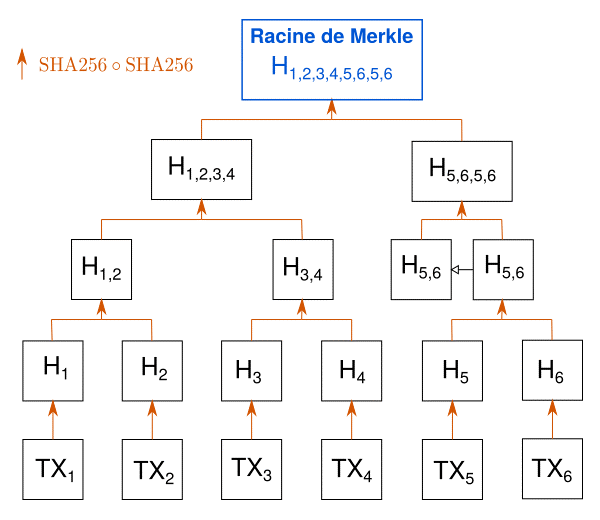
Transactions are hashed, then their fingerprints are hashed two by two to get only one root.
The most famous portfolio that uses this technique in a classic way is BRD. There is also Electrum, which however does not do the same thing: Electrum does request information from a subset of specialized nodes in the network, called Electrum servers (using ElectrumX), rather than from all nodes in the network.
These wallets, of course, have drawbacks and trade-offs. The first compromise concerns security: when accessing nodes on the network, wallets of this type trust them and provide the necessary information. However, this is a partial problem, since nodes can only ignore the fact of the transaction, and not create it from scratch. Thus, by connecting to a sufficient number of nodes, you can imagine that the wallet will receive the necessary information from them.
The second compromise is user privacy. Indeed, if implemented naively, this type of client is problematic, since the nodes it connects to can easily guess what transactions it has in the chain. Fortunately, there are ways to mitigate this problem. These are the widespread bloom filters (bip37), which provide relative privacy in addition to increasing synchronization speed.
To ensure availability for users who do not have a full node, ligthning network solutions are also being developed.
Thus, the solution to the problem of access to cryptocurrencies is already there. In the future, it will be necessary to improve the user experience of various wallets and find other ways, for example, to make offline payments (in the case of a place without the Internet). However, this is a very good start.
Second problem: managing private keys

The case of Peter Schiff’s asset loss proves that many people don’t understand (and some will never understand) how the system works. One thing is for sure: private key management needs to be improved.
A private key is an information that is used to control funds held at a public address. Roughly speaking, a private key is a password that gives access to your Bitcoin “account”. If someone gets it, he will be able to steal your crypto located at this address. And if you lose it, the precious coins will be lost forever (which is what happened to Peter Schiff). In most cases (and to preserve your privacy), your wallet will need to create multiple addresses to receive funds. This way you will have a lot of private keys to manage.
Initially, the private keys were generated by the program and stored in the wallet.dat file, so they were very difficult to save. However, after 2012, a standard was developed that allows private keys and addresses to be extracted from the same passphrase (consisting of 12-24 words), called the recovery phrase. This made it much easier to back up: then only a suggestion was enough to find the funds in the wallet.
If this standard made life easier for programmers, it did not solve the main problem: the user must somehow save this offer, and if he does not do this, he risks losing his funds. Informing people about is crucial, but as already mentioned, many people will not listen anyway and will lose their cryptocurrency. So if we want to democratize cryptocurrency, we have to find another solution.
There is no perfect solution to this problem. Indeed, we want the user to continue to control their money, and we need to prevent someone else from managing the keys. However, several attempts have been made to correct this.
First, we can refer to the system created by Edge and Blockchain.com wallets which allow a crypto holder to log in with an alias and password from any device – a process familiar to most. Private keys are encrypted with a password and stored in this form on the company’s servers, so that the user (if he did not write down his recovery phrase) will be able to recover his funds, since he remembers his IDs. Even if this solution is a compromise and far from ideal, it will appeal to many people who do not use their wallet to transfer large amounts.
The second solution, which seems much more appropriate for cryptocurrency , is to use offline contracts to set up the recovery process. This is the case with the last will protocol on bitcoin cash, which allows pre-designated persons to return funds from your wallet (this can be a registry) if you do not complete the transaction within a certain period of time (say a year). This protocol is called Last Will, and it is designed to facilitate inheritance.
As for Ethereum, we have a great example of a Silver wallet that uses a well-designed contract to help users regain access to their account through a security system.
Conclusion
So, while the interface with cryptocurrency is still difficult, it is improving day by day thanks to the hard work of thousands of enthusiasts who want to see democratization take place in a decentralized manner. The problems hindering the popularization of cryptocurrencies still exist, but it is likely that they will be solved in the coming years.


